The vision of IoT is the intelligent connectivity, sensing, control, and management of a wide range of physical and “smart” devices, vehicles, and energy and power management in buildings.
By 2020, industry experts estimate that the IoT will consist of over 30 billion objects; per the CEO of Cisco, the commercial opportunity for “connected products ranging from cars to household goods” is expected to reach $19 trillion. Remote access and intelligent interoperability of disparate devices and systems across a data network is expected to automate technology solutions in every major field and improve efficiency and economic value via reduced human intervention.
Current industry examples showcase smart cars and intelligent building systems controlling lighting, ventilation, HVAC systems and security. Environmental monitoring of our water quality, atmosphere, and soil conditions for farming play a key role in our society. Healthcare organizations are beginning to deploy smart beds and outsourcing remote health and heart monitoring services and devices. Tied to emergency notification response companies, these solutions are designed to improve out-patient healthcare and reduce costs.
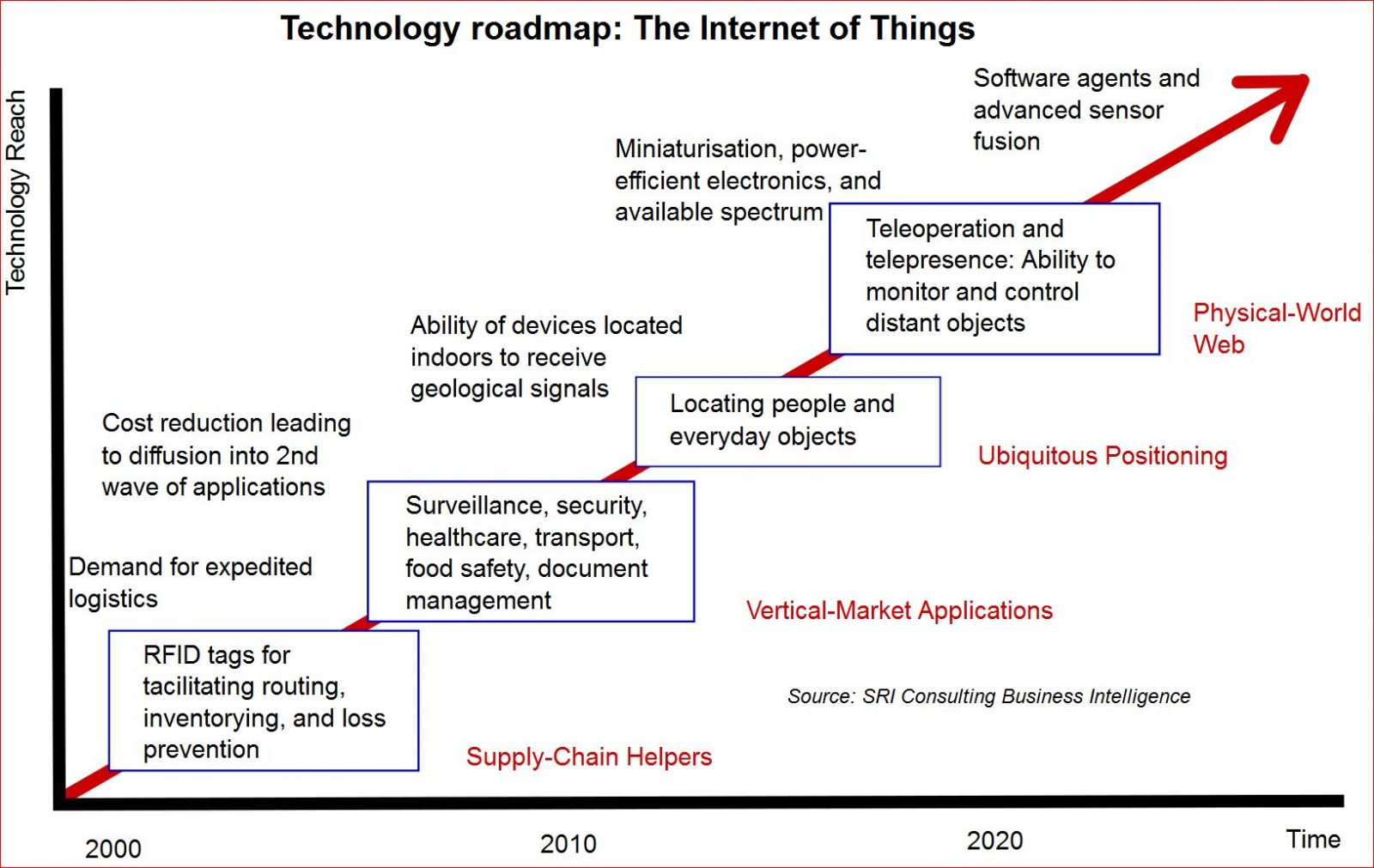
Graph: Wikipedia
IoT is also expected to generate large amounts of user data, giving rise to the need to aggregate, index and store collected data. Many devices collect useful information while others may in turn resell it for marketing purposes with or without a user’s permission. A recent example is the lawsuit filed against Bose for collecting and selling subscriber usage data from headphones without permission.
In addition to data privacy, challenges can include the deployment of devices using proprietary hardware and platforms that make it difficult and expensive to integrate and interconnect. But the biggest identified risk is security Allowing unauthorized and unsecured access to enterprise systems through personal and IoT devices without certification, testing or network segregation can increase vulnerability to cyber-attacks, denial of service (DOS) attacks and system outages.